Database Browser
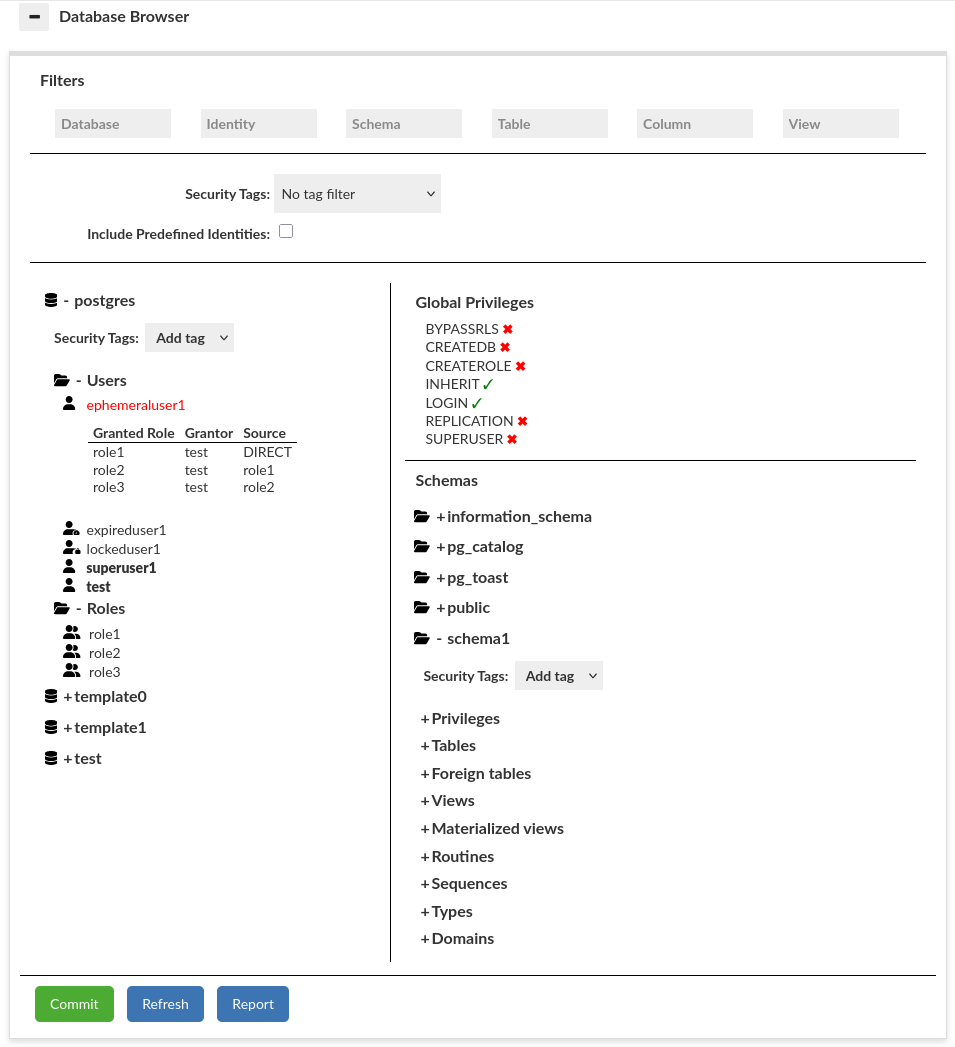
The Database Browser is a versatile tool designed for viewing database structures and modifying permissions. It operates on multiple levels to provide detailed access and control. It is possible to filter resources or assign a security tag.
Data Source User
Ensure that the configured Data Source user has the superuser privileges (i.e. highest privileges). This is necessary because we need to get information about other users and their privileges. Without the highest privileges, the Database Browser may function incorrectly, leading to potential issues such as inaccurate information and the inability to update privileges.
Supported Database Types
The supported databases are PostgreSQL, Greenplum, Redshift, MySQL, SQLServer, and Oracle.
Warning in MySQL: This feature is NOT functional when using MySQL with version < 8.0.
Warning: Reports in MySQL and SQLServer with aggregated permissions are not functional yet.
Database Structure
Databases
The entry point where you select the database to work with.
Identities
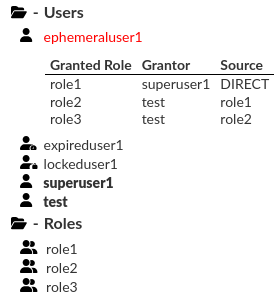
The identity means user (can log in) or role (cannot log in). Identities are categorized into catalogs. In each database, you can select a specific identity to check its privileges and its role inheritance. Moreover, we can easily determine if selected identity is a superuser, a predefined identity, its account is locked, its password is expired. A selected identity will be highlighted in red. Bold text indicates the superusers, and other icon marks the expired or locked identities.
Information: Only in Redshift there is an additional section for groups.
Global Privileges

Global privileges, often referred to as system privileges in some databases, are permissions granted to users that apply at the system or database level, rather than being tied to specific objects like tables or schemas. They typically allow users to perform administrative or high-level operations, such as creating objects, managing users, or connecting to the database, and may override more granular, object-specific permissions.
Schemas
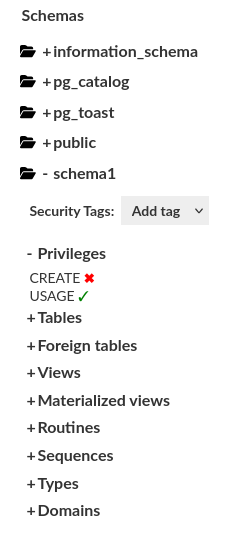
Access and manage schemas. You can see and modify schema permissions of selected identity.
Information: Currently, only the tables and views are supported in every database type, and we are in process to extend this to cover all database objects that we can grant privileges to. The idea remains the same.
Tables
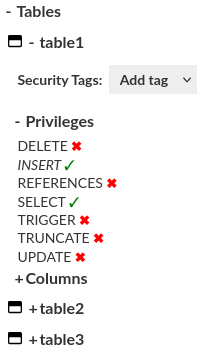
Access and manage tables. You can see and modify table permissions of selected identity.
Views
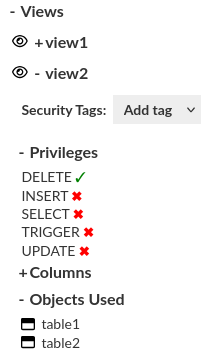
Access and manage views. You can see which views and tables are used by selected view. You can see and modify view permissions of selected identity.
Columns
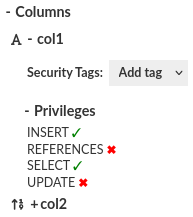
Access and manage columns. You can see and modify column permissions of selected identity.
Aggregated Privileges
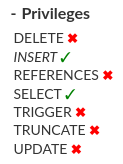
Every object contains Privileges section, where we provide information about the aggregated privileges. You can manage them by clicking the ✓ or ✖ near the permission and then click the Commit button to save the updated permission.
Information: Privileges can come from different sources. Below is a list containing our API keywords and the corresponding queries needed to achieve each type of grant. Warning: It is revoking operation is possible only when the privilege is granted directly on the selected identity. The privilege that is not granted directly is in italics.
Newest data
By clicking the Refresh button you can fetch the newest data.
Audit Reports
By clicking the Report button you can generate and download a report of the data source structure for the currently selected filters. This report provides a JSON view of all the users and roles configured on the database, and all the access down to the column level the users and roles have. The report can be considered a form of credential discovery, specific for the database, and helps to normalize audits of different database types. The call to generate this report can be triggered with an automated API call, so can tie in with a periodic auditing system that spots changes to the permissions for a compliance team.
Each non-column element of the report has a checksum calculated from its direct components. Checksums do not include deeper nested subcomponents. They are also not guaranteed to remain the same for different report filters.
PostgreSQL, Greenplum, Redshift
Warnings
Our API shows aggregated privileges with source. Be aware of "hidden" privileges when inheritance occurs due to a lack of the USAGE privilege on the schema level.
Information
In PostgreSQL/Greenplum/Redshift access to objects in a schema requires:
- Privileges on the object (e.g., SELECT, INSERT).
- The USAGE privilege on the schema to make the object accessible.
If a role lacks USAGE on the schema, any privileges it has on objects in that schema remain hidden and unusable. These privileges become active if USAGE is granted or inherited.
Example:
- Role A has a SELECT on schema1.table1 but no USAGE on schema1.
- Role A cannot access schema1.table1 until USAGE on schema1 is granted.
- If Role B inherits Role A and has USAGE on schema1, Role B gains access to schema1.table1.
Privilege Sources
- GRANTED DIRECTLY
- "GRANT privilege ON object TO identity"
- "ALTER ROLE identity privilege"
- "GRANT privilege ON SCHEMA schema TO identity"
- "GRANT privilege (column) ON TABLE object TO identity"
- PUBLIC ON OBJECT
- "GRANT privilege ON object TO public"
- INHERITED FROM IDENTITY ON OBJECT (includes nested identities)
- "GRANT privilege ON object TO identity" with "GRANT role TO identity"
- SUPERUSER (mean access to every resource)
- "ALTER USER identity SUPERUSER" or "ALTER ROLE identity SUPERUSER"
MySQL
Warnings
The PROXY global privilege is not shown yet.
Privilege Sources
- GRANTED DIRECTLY
- "GRANT privilege (column) ON object TO identity"
- "GRANT privilege ON object TO identity"
- "GRANT privilege ON schema.* TO identity"
- "GRANT privilege ON *.* TO identity"
- INHERITED FROM OBJECT (visible when viewing privileges on column level)
- "GRANT privilege ON object TO identity"
- INHERITED FROM SCHEMA (visible from tables/columns in the schema)
- "GRANT privilege ON schema.* TO identity"
- INHERITED FROM GLOBAL PRIVILEGE (visible from any schema/object)
- "GRANT privilege ON *.* TO identity"
- INHERITED FROM IDENTITY ON COLUMN (includes nested identities)
- "GRANT privilege (column) ON object TO role" with "GRANT role TO identity"
- INHERITED FROM IDENTITY ON OBJECT (includes nested identities)
- "GRANT privilege ON object TO role" with "GRANT role TO identity"
- INHERITED FROM IDENTITY ON SCHEMA (includes nested identities)
- "GRANT privilege ON schema.* TO role" with "GRANT role TO identity"
- INHERITED FROM IDENTITY GLOBAL PRIVILEGE (includes nested identities)
- "GRANT privilege ON *.* TO role" with "GRANT role TO identity"
Oracle
Privilege Sources
- GRANTED DIRECTLY
- "GRANT privilege ON object TO identity"
- "GRANT privilege (column) ON TABLE object TO identity"
- "GRANT privilege TO identity"
- PUBLIC ON OBJECT
- "GRANT privilege ON object TO public"
- INHERITED FROM ROLE ON OBJECT (includes nested roles)
- "GRANT privilege ON object TO role" with "GRANT role TO identity"
- PUBLIC SYSTEM PRIVILEGE
- "GRANT system_privilege TO public"
- INHERITED FROM SYSTEM PRIVILEGE (includes nested roles)
- "GRANT system_privilege TO role" with "GRANT role TO identity"
- OWNER OF TABLE
- "CREATE TABLE..." - if the identity created the table, he has all privileges to it
- OWNER OF VIEW
- "CREATE VIEW..." - if the identity created the view, he has all privileges to it
- OWNER OF COLUMN
- "CREATE TABLE/VIEW..." - if the identity created the table/view, means columns also, he has all privileges to it
- INHERITED FROM OBJECT
- if the privilege was granted on the table/view level, means it is inherited on the column level also
SQLServer
Information
Under the database section, in SQLServer and Babelfish two additional catalogs are provided with Server Users and Server Roles.
Privilege Sources
- GRANTED DIRECTLY
- "GRANT privilege (column) ON OBJECT::object TO identity"
- "GRANT privilege ON object TO identity"
- "GRANT privilege ON SCHEMA::schema TO identity"
- "GRANT privilege TO identity"
- PUBLIC ON COLUMN
- "GRANT privilege (column) ON OBJECT::object TO public"
- PUBLIC ON OBJECT
- "GRANT privilege ON OBJECT::object TO public"
- PUBLIC ON SCHEMA
- "GRANT privilege ON SCHEMA::schema TO public"
- PUBLIC GLOBAL PRIVILEGE
- "GRANT privilege TO public"
- OWNER OF TABLE
- "ALTER AUTHORIZATION ON OBJECT::object TO identity"
- OWNER OF SCHEMA
- "ALTER AUTHORIZATION ON SCHEMA::schema TO identity"
- PUBLIC OWNER OF TABLE
- "ALTER AUTHORIZATION ON OBJECT::object TO public"
- PUBLIC OWNER OF SCHEMA
- "ALTER AUTHORIZATION ON SCHEMA::schema TO public"
- INHERITED FROM ROLE OWNER OF TABLE (includes nested roles)
- "ALTER AUTHORIZATION ON OBJECT::object TO role" with "ALTER ROLE role ADD MEMBER identity"
- INHERITED FROM ROLE OWNER OF SCHEMA (includes nested roles)
- "ALTER AUTHORIZATION ON SCHEMA::schema TO role" with "ALTER ROLE role ADD MEMBER identity"
- INHERITED FROM ROLE ON COLUMN (includes nested roles)
- "GRANT privilege (column) ON OBJECT::object TO role" with "ALTER ROLE role ADD MEMBER identity"
- INHERITED FROM ROLE ON OBJECT (includes nested roles)
- "GRANT privilege ON OBJECT::object TO role" with "ALTER ROLE role ADD MEMBER identity"
- INHERITED FROM ROLE ON SCHEMA (includes nested roles)
- "GRANT privilege ON SCHEMA::schema TO role" with "ALTER ROLE role ADD MEMBER identity"
- INHERITED FROM ROLE GLOBAL PRIVILEGE (includes nested roles)
- "GRANT privilege TO role" with "ALTER ROLE role ADD MEMBER identity"
- INHERITED FROM OBJECT (visible when viewing privileges on column level)
- "GRANT privilege ON object TO identity"
- INHERITED FROM SCHEMA (visible from tables/columns in the schema)
- "GRANT privilege ON SCHEMA::schema TO identity"
- INHERITED FROM GLOBAL PRIVILEGE (visible from any schema/object)
- "GRANT privilege TO identity"
- INHERITED FROM CONTROL ON OBJECT (visible on privileges on column and object level)
- "GRANT CONTROL ON object TO identity"
- INHERITED FROM CONTROL ON SCHEMA (visible on privileges on column, object and schema level)
- "GRANT CONTROL ON SCHEMA::schema TO identity"
- INHERITED FROM GLOBAL CONTROL ON DATABASE (visible on privileges on column, object, schema and database level)
- "GRANT CONTROL TO identity"
- INHERITED FROM GLOBAL CONTROL ON SERVER (visible on any privilege except CONTROL SERVER)
- "GRANT CONTROL SERVER TO serverIdentity"
- INHERITED FROM OTHER GLOBAL PRIVILEGE (visible on privileges granted by other privileges)
- "GRANT privilege TO serverIdentity/identity"
- INHERITED FROM SPECIAL DATABASE ROLE (visible on privileges granted by special database roles)
- "ALTER ROLE specialRole ADD MEMBER identity"
- INHERITED FROM SPECIAL SERVER ROLE (visible on privileges granted by special server roles)
- "ALTER SERVER ROLE specialRole ADD MEMBER serverIdentity"
- INHERITED FROM SYSADMIN (visible on schema, object and column level when login is member of sysadmin role)
- "ALTER SERVER ROLE sysadmin ADD MEMBER serverIdentity"