Heimdall Access Gateway with SailPoint Integration
Objective
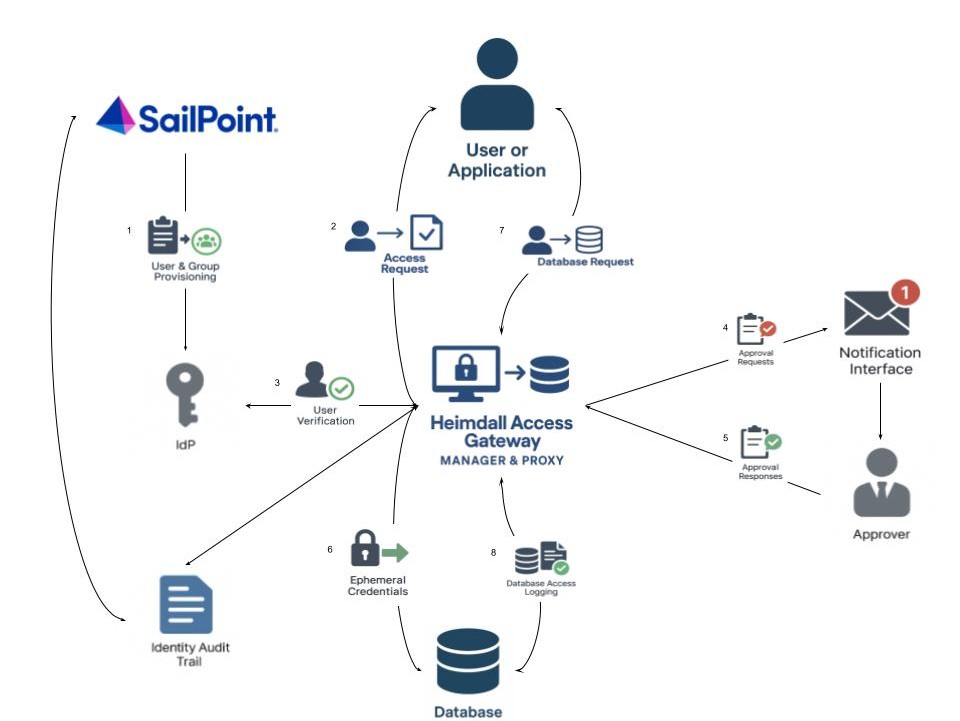
This document explains the flow of secure and audited database access using the integration of Heimdall Access Gateway with SailPoint Identity Governance. It ensures access is policy-driven, ephemeral (temporary), and fully traceable.
Overview of Components
- SailPoint – Identity management system responsible for provisioning and governance.
- Heimdall Access Gateway – Acts as a secure proxy between users/applications and databases.
- Identity Provider (IdP) – Verifies user identity before access is granted.
- Notification Interface (Heimdall Manager) – Centralized dashboard managing approval workflows, notifications, and audit logs.
- Database – Target system that users/applications need to access.
- Approver – User or admin responsible for approving access requests.
Step-by-Step Access Flow
1. User & Group Provisioning
The process begins with SailPoint performing user and group provisioning. This includes:
- Creating identities in a central Identity Provider (IdP),
- Assigning roles and access policies,
- Ensuring the right individuals have the right access to the right systems.
This step guarantees that all users and groups are pre-configured and synchronized with SailPoint for lifecycle and access governance.
2. Access Request
Once the user is provisioned, they (or their application) initiate an access request to gain entry to a target database. This request is routed through the Heimdall Access Gateway which acts as an intermediary enforcing access control logic.
3. User Verification
The Heimdall Gateway communicates with the Identity Provider (IdP) to verify the user’s identity:
- Using standard authentication protocols (SAML).
- Ensuring the user is authorized based on the identity attributes and role mappings provisioned by SailPoint.
Only verified users can proceed to the next stage.
4. Approval Request
If additional approval is required before database access, Heimdall sends an approval request to the designated approver via Heimdall Notification Interface:
- This can be an email or Heimdall workflow system.
- Triggers an alert to relevant stakeholders indicating a pending access request.
5. Approval Response
The approver reviews the access request and responds via the Heimdall notification interface:
- Approving or rejecting the request based on contextual information.
- The response is captured and routed back to Heimdall Access Gateway for enforcement.
6. Ephemeral Credentials
Upon receiving approval (if required), Heimdall dynamically generates ephemeral credentials:
- These are short-lived, one-time-use credentials to access the target database.
- Enhances security by avoiding static or long-term credential exposure.
These credentials are issued only for the duration and scope of the approved access.
7. Database Request
The user or application then submits their database query request using the ephemeral credentials:
- Heimdall proxies the request to the backend database.
- It ensures the request complies with access rules and usage policies.
8. Database Access Logging
All interactions between users and the database are logged by Heimdall:
- This includes query logs, timestamps, and user details.
- The logs are sent to an Identity Audit Trail system (e.g., integrated with SailPoint or SIEM).
- Facilitates compliance reporting, forensic analysis, and security audits.
Security and Compliance Highlights
- Zero standing access: Credentials are generated only when needed.
- Audit ready: Every access is logged and traceable.
- Approval workflow integration: Adds governance and oversight to sensitive operations.
- Seamless authentication: Integrated with your existing Identity Provider (e.g., AD etc).